Introduction
In today's interconnected digital landscape, where information flows seamlessly and transactions occur at the speed of thought, safeguarding our virtual domains has become paramount. Cybersecurity, the steadfast guardian against a relentless tide of evolving threats, stands as our sentinel in this era of connectivity. Amid the perpetual cat-and-mouse game with malicious actors, the concept of the adaptive security system emerges as a beacon of modern defense. As breaches grow in sophistication, an adaptive security system's proactive stance and dynamic resilience have become indispensable shields, fortifying our data, privacy, and digital lives against an ever-changing adversary.
Understanding Adaptive Security Systems
Adaptive security systems are designed to continuously evolve, learn, and respond in real-time to emerging threats and attack vectors. Unlike rigid security solutions that rely on fixed rule sets, adaptive systems possess the ability to autonomously adjust their defenses based on the ever-changing threat landscape. This adaptability is rooted in technologies such as machine learning, artificial intelligence, and behavioral analysis, which collectively empower these systems to recognize patterns, detect anomalies, and predict potential threats before they materialize into full-blown attacks.
Traditional Security Systems vs. Adaptive Security Systems: A Comparative Overview
| Aspect | Traditional Security Systems | Adaptive Security Systems |
|---|---|---|
| Response to Emerging Threats | Relies on signature-based detection, effective against known threats but struggles with novel attacks | Utilizes machine learning and AI to recognize patterns of both known and new threats, adapting to evolving attack methods |
| Static vs. Dynamic Defenses | Often employs static defense posture requiring manual updates | Utilizes dynamic defenses that can adjust and learn from new data, improving responses over time |
| False Positive Rates | Can have higher false positive rates due to limited analysis capabilities | Reduces false positives through behavioral analysis and AI-driven decision-making |
| Detection of Insider Threats | Struggles to detect insider threats due to reliance on signatures | Excels at detecting insider threats by monitoring deviations from established user behavior patterns |
| Real-time Monitoring | Involves periodic scanning and manual log analysis, leading to delays | Offers continuous real-time monitoring for immediate threat identification and response |
| Customization and Context | Lacks understanding of organization's context, resulting in less relevant defenses | Customizable to organization's specific requirements, considering industry, compliance, and unique threats |
| Automation and Incident Response | Relies on manual intervention, causing potential delays and errors | Incorporates automation for faster, consistent incident response and mitigation |
The Adaptive Security System stands as a remarkable evolution in cybersecurity, offering a departure from the limitations of traditional approaches. By embracing adaptability, intelligence, and real-time responsiveness, adaptive security systems hold the potential to thwart the ever-evolving threat landscape more effectively, providing organizations with a robust and dynamic defense mechanism against cyber threats.
Key Components of an Adaptive Security System
The key components of an adaptive security system include:
- Continuous monitoring: This involves the use of advanced analytics and machine learning algorithms to monitor network traffic and user behavior continuously. It helps in identifying unusual patterns or anomalies that may indicate a potential security threat. Continuous monitoring provides real-time visibility into the network, enabling quick detection and response to threats.
- Threat intelligence: This involves gathering and analyzing information about potential or existing threats to help organizations understand and mitigate them. Threat intelligence can come from various sources, including open-source intelligence, social media intelligence, human intelligence, and technical intelligence. It provides insights into the tactics, techniques, and procedures used by cybercriminals, helping organizations to stay one step ahead of them.
- Risk assessment: s identifying, assessing, and prioritizing risks to the organization’s information assets. The risk assessment process helps in understanding the potential impact of a security breach and enables organizations to allocate resources effectively to mitigate those risks.
- Threat response: Automated responses are a critical aspect of adaptive security systems. When a potential threat is identified, the system can automatically trigger predefined responses. For instance, it might isolate an affected system from the network, block traffic from suspicious IP addresses, or initiate incident response protocols. Automated responses help contain threats quickly, minimizing potential damage.
- Threat prediction: The final component of an effective adaptive security architecture is predictive analytics. This involves using data, statistical algorithms, and machine learning techniques to identify the likelihood of future outcomes based on historical data. Predictive analytics can help organizations anticipate potential threats and take proactive measures to prevent them. It helps in anticipating and preparing for new or evolving attacks before they occur.
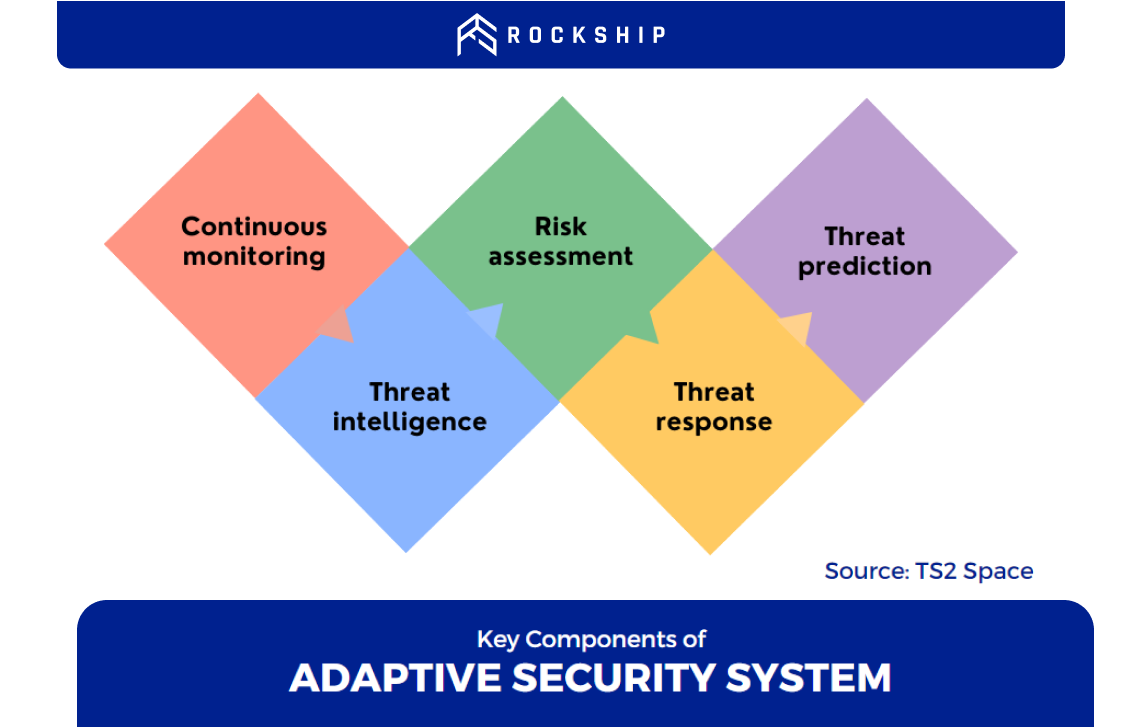
These components work together to create a feedback loop of threat visibility, detection, prevention, and prediction that constantly improves the security posture of the system. An adaptive security system is flexible, resilient, and agile in responding to the dynamic and complex cyber environment.
Real-life Use Cases
Adaptive security systems have gained popularity in various industries as organizations aim to strengthen their defenses against ever-changing cyber threats. One standout example is Darktrace, a cybersecurity company founded in 2013. They're known for introducing self-learning artificial intelligence to create an adaptable defense system inspired by the human immune system. A highlight from Darktrace is the "Darktrace Enterprise Immune System," a product designed to quickly spot and counter emerging cyber threats in real-time.
At the heart of Darktrace's adaptive security system is a foundation of machine learning and AI algorithms. These algorithms build a flexible baseline that reflects an organization's network, devices, and user behaviors. This baseline keeps updating as the system learns the unique activity patterns of the organization. This way, the system becomes very good at spotting even slight deviations that could indicate a breach or something unusual.
One impressive thing about Darktrace is its ability to find new threats that haven't been seen before, often called zero-day attacks. These attacks exploit vulnerabilities that haven't been revealed to the public or security experts yet, making them tricky for traditional security methods.
In a real-world example, a financial company adopted Darktrace's solution to protect its network. During a regular check, the system noticed unusual patterns of data leaving a server that had never shown signs of compromise before. This unusual behavior looked like a zero-day attack, involving a new type of malware trying to steal important data.
Darktrace's adaptive security system quickly sent an alert, so the security team started investigating. They found evidence of a clever attack exploiting an unknown weakness. Thanks to Darktrace's warning, the financial company acted fast to stop the threat, limit the damage, and fix the vulnerability before the attack could spread.
Conclusion
As you have seen, adaptive security systems offer a powerful way to stay ahead of today's sophisticated cyber threats. By leveraging AI and machine learning, adaptive systems get smarter over time and can detect anomalies and zero-day attacks traditional tools would miss. They adapt to your unique environment and threat landscape, providing customized protection. While adaptive security does require investment, the potential costs of a breach far outweigh the costs of proactively defending your network. For any organization looking to strengthen their cyber defenses, exploring adaptive security solutions is a step in the right direction towards a safer digital future. The power to adapt is the power to survive and thrive. Adaptive security helps ensure you have that power.